How to Ensure Secure Video Sharing for Enterprises
by Rafey Iqbal, Last updated: February 26, 2026, ref:
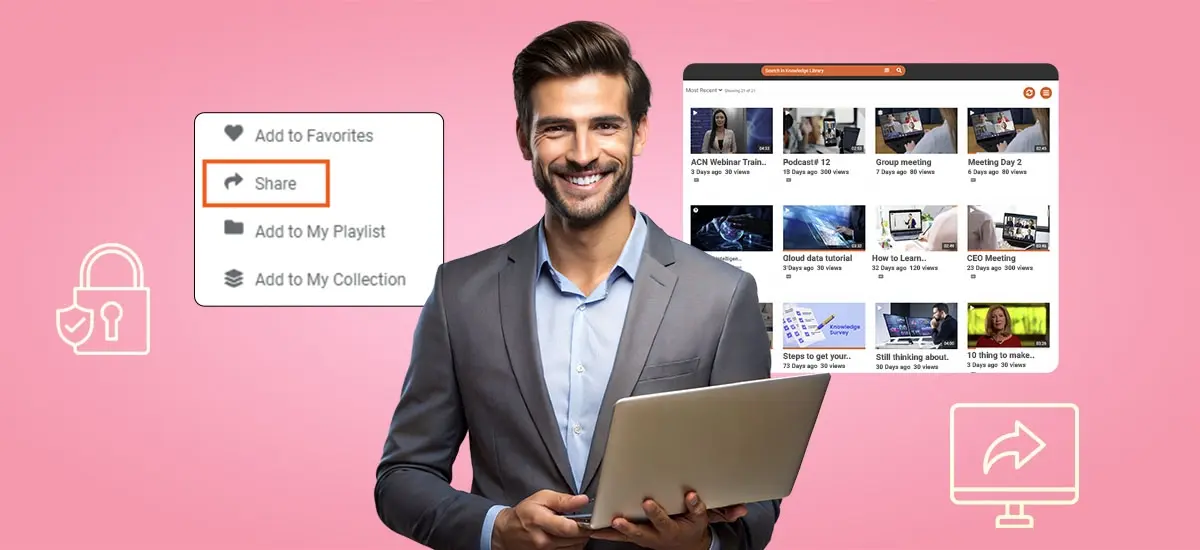
Secure video sharing helps businesses protect sensitive content from leaks and unauthorized access. For enterprises, reliable secure video content delivery and private video sharing workflows ensure that sensitive recordings stay controlled, compliant, and easy for authorized teams to access. This blog explores 10 best practices, like password protection, encryption, and access controls, and key considerations to keep video sharing private and compliant.
With companies increasingly using videos to perform business operations, it is understood that many of these videos contain sensitive, commercial information that businesses cannot afford to have leaked. This is why secure video content delivery sharing is gaining wide acceptance among enterprises.
After all, there is a rich history of enterprises accidentally leaking their confidential, private videos to the public eye. These videos included upcoming product videos and private videos of customers.
According to a study by Varonis, a typical company shares its business content with over 800 parties. You can imagine how hard it would be to keep track of the practices involved in sharing video content online.
And if you still think that sharing files over a “secure” email server is the answer you were always looking for, think again. The 2024 Email Security Risk Report by Egress reveals that emails are found guilty in about 94% of data security incidents within companies.
This is why we have written this detailed blog to inform you of the best practices for secure video sharing and cover several factors that you need to consider when securely sharing videos online.
But before discussing the best practices for private video sharing, it's wise to understand secure video sharing and why it is essential. We promise it’ll be short.
What is Secure Video Sharing?
Secure video sharing involves sharing videos privately with internal and external recipients in organizations. This is done by placing appropriate restrictions to ensure that transparency and privacy go hand in hand.
Private video sharing is of immense significance to enterprises. Take the example of corporate communications.
When communicating with employees and other stakeholders through video, certain types of enterprise video content, including CEO communication videos, town hall meeting videos, internal company announcement videos, etc., are involved.
Let’s take another example, this time, healthcare. The healthcare industry deals with sensitive patient information found in several audio/video recordings. These videos also need to be shared securely with extreme care and vigilance, given the high stakes of data privacy involved.
Secure Video Content Delivery Platforms make sure that the data can only be viewed by people who are given rights to.
Factors to Consider for Secure Video Sharing in Enterprises
Before going for secure video sharing, you need to consider some factors so that you can decide how secure or foolproof your private video sharing should be and ensure that the integrity of your shared data is not harmed in any way.
We have compiled a list of factors phrased as questions you need to ask so that you can make a wise decision before hitting the Share button:

- How sensitive is the video you’re going to share?
- Who will be the video recipient?
- What type of information is found in the video?
- Are there any compliance governing data sharing in your industry or region?
- For how long should access to the shared video be given?
- What level of shared access should be given to the recipient?
- Is there any chance that unauthorized people can get their dirty hands on the video?
- What if the shared video falls into the wrong hands?
- Does the shared video need to be downloaded by the recipient?
- What does your company's data sharing agreement say about secure video sharing?
Now, let’s break down the above one-liners into detail to better understand the factors to consider for private video sharing:
Sensitivity of Video Content
The sensitivity of the enterprise video content is directly related to the measures you need to take for secure video content delivery. For instance, a video of an organizational training program contains information regarding the internal processes and frameworks used in the company.
Compared to the employee training video, a CEO/executive communications video regarding an upcoming product is way more sensitive since it contains proprietary information regarding the to-be-announced product. The stakes are much higher in this one.
Video Recipients
Whether you will share the video content internally within the organization or externally with third parties is another point of consideration for secure video sharing. For instance, the investor relations department might share an investor relations video with their existing and prospective financial investors.
In another case, the human resources department will need to share a town hall meeting video with the company’s employees. Similarly, a healthcare facility might need to share a patient experience video with the internal staff for patient education purposes.
Type of Information
The type of information being shared in the video is also considered an important factor for private video sharing. This helps in deciding whether the video is internal, confidential, or restricted according to the business data classification levels.

For instance, a video recording of a board of directors’ meeting might be considered restricted since it is only made available to the senior management of the company. Similarly, a sales training video is considered confidential since a particular team can access it.
Having a clear understanding of the type of information being shared in videos helps you decide how vigilant you should be when you share private videos like the ones mentioned above.
Compliances
With businesses caught in the clutch of regional, industry-specific, and other data privacy compliances, companies cannot help but consider compliance before performing secure video sharing. Some of the common compliances are GDPR, HIPAA, and CCPA.
A patient consultation video in the healthcare setting falls under HIPAA compliance since it contains sensitive patient information. Therefore, such healthcare settings need to have secure healthcare video hosting. Similarly, CCTV footage in retail stores is subject to GDPR or CCPA, in case the store is based in California, since it contains people's identifiable faces.
Access Duration
Not all private enterprise video content lasts. While there is no rulebook for which videos should be available for how long, a general thumb rule is that the greater the sensitivity of the video content, the lower the access duration.
For instance, a video regarding an undisclosed future M&A deal should be shared for a limited time since leaving it idle for a long time can lead to data leakage. Other cases where temporary video share might be the best secure video sharing option are investor relations videos, internal video announcements, change management videos, etc.
Access Level
When you share private videos, one thing you need to consider is what access level should be given to whom when securely sharing your enterprise video content online. In some cases, you might need to give editing rights to the recipient so that they can further annotate or make modifications to the video. In other cases, giving viewing rights might be enough.
For instance, a video production manager responsible for contributing to marketing collateral might need to share a video with their team to get their input. In that case, they need to give adequate editing rights without compromising the security of the shared video.
In another instance, you will share an annual general meeting (AGM) recording with a view-only access so that all employees throughout the organization can watch it.
Risk of Unauthorized Access
Some videos are so sensitive that unauthorized people try to get their hands on them fwhile risking data privacy and the company’s reputation. This will affect how strong your secure video sharing game should be.
This is why you need to thoroughly analyze whether sharing a particular video has a greater risk of unauthorized access. In that case, you will need to take extreme measures to share your videos securely.
Corporate videos containing proprietary information, such as product videos shared within the R&D team of an organization, might be at a greater risk of unauthorized exposure. With that said, you will need to take extra measures to ensure highly secure video sharing
Implications of Unwarranted Access
What if the confidential video falls into the wrong hands? What bad could happen? These are the questions you need to ask yourself before you share private videos.
Take the example of a video discussing an upcoming product that has not yet been announced in the press. The video should not get out, or else the hype for the upcoming product will be dead, and your launch event will be a failure.
In the healthcare industry, the stakes are equally high, if not higher. In case HIPAA identifiers and patient information get leaked from consultation recordings, your healthcare entity will need to pay loads of cash for not complying with HIPAA.
To Download or Not to Download
One of the risks involved with sharing an enterprise video is that the recipient might download it. This recipient can, intentionally or unintentionally, share this video with unauthorized external parties.
The good news is that secure video-sharing platforms come with download restriction capability. You can simply allow or disable the downloading of the video as you wish.
You should not make available sensitive enterprise video content, such as company town hall meetings, internal communications videos, etc., for download by recipients. Otherwise, these videos can go beyond the four walls of the organization, causing trouble for your company.
Company Data Sharing Policy
Your company’s data sharing agreement (DSA) also plays a significant role in determining the amount of effort you need to put into private video sharing. The agreement offers information on the rules regarding the sharing of identifiable information, confidential commercial information (CCI), trade secrets, etc.
For instance, a company might share the personal or health information of an individual found in videos with law enforcement officials in line with its data-sharing agreement. Another company might only share the bare minimum information while redacting portions of the enterprise video content.
10 Best Practices for Secure Video Sharing
Since we have understood the factors involved in secure video sharing, it is now time to look at the ten best practices for private video sharing. The following actionable tips will help you explore how to share videos privately:

- Protect videos with password-protected video sharing
- Restrict access to enterprise video content
- Secure videos with temporary video share
- Authenticate users for secure video sharing
- Define a custom security policy
- Enable IP and location restrictions
- Blacklist domains for secure media embedding
- Share videos with encrypted video sharing
- Redact sensitive content from videos
- Restrict the downloading of videos
The following illustration offers a bird's-eye view of when to follow a particular secure video sharing best practice.
Let’s explore each best practice that guides you on how to share a private video in enterprises:
Protect Videos with Password-Protected Video Sharing
One of the simplest forms of password protected video sharing is adding a complex password to your enterprise videos. While password protected video hosting is useful for low-sensitivity content, high-security use cases should combine it with IAM-based secure video file sharing and encryption. Despite its simplicity and ease of implementation, password-protected video sharing is an effective way to share private videos.
Passwords are a best fit for secure video sharing in the following cases:
- The sensitivity of video content is relatively low.
- You want to share a single video with recipients who grow over time.
- The type of information is internal according to the business data classification level.
- You don’t need to comply with data privacy laws and regulations.
- The implications of unwarranted access are negligible.
For instance, company profile videos or employee onboarding videos shared with new hires can be password-protected since they do not contain a high level of sensitive information that could hurt the business if unauthorized people access them.
Restrict Access to Enterprise Video Content
Restricting access to enterprise video content is more effective than simply protecting it using a password. By limiting access to enterprise video content with a granular role-based access control mechanism, you can assign user roles to different people.
This helps in preventing malicious insider threats within organizations. According to the 2023 Insider Threat Report by Cybersecurity Insiders, 74% of companies have admitted that insider attacks have become quite common.
In case predefined user roles are not enough to cater to your secure video sharing needs, you can define and apply user and group permissions the way you like them. This allows for a tailored approach to private video sharing.
Restricting access to enterprise video content works fine in the following cases:
- The sensitivity of video content is moderate or high.
- You want to share multiple videos with recipients that grow over time.
- The type of information in videos is confidential or restricted.
- Data privacy compliances apply to the video content you share.
- You need to give different access levels to different recipients.
- There is a risk of unauthorized access by hackers or corporate espionage agents.
- The implications of unwarranted access are damaging to your company.
For instance, team meeting videos, employee training videos, and patient consultation videos should be shared with restricted access since they contain highly sensitive information subject to compliance, such as HIPAA, and their disclosure can hurt the business in terms of reputation or leakage of trade secrets.
Secure Videos with Temporary Video Share
Secure video sharing using temporary video share allows you to share a private video for a limited time or limit it by the number of times the recipients can access it. With a secure temporary link to the shared video, you can ensure that the video content no longer remains with the recipient when the purpose is fulfilled.
We recommend securing videos with temporary video share in the following cases:
- The sensitivity of video content is high or extremely high.
- You want to share the video with multiple recipients outside your organization.
- The type of information shared in the video is of a restricted nature.
- The video content falls under the scope of data privacy compliance.
- You need to give timed access to shared video recipients.
- You need to give different access levels to the people you’re sharing the video with.
- Unauthorized access can cause severe damage to breach of privacy and data.
For instance, you should temporarily share investor relations videos shared with your company’s external stakeholders since they contain sensitive financial and confidential commercial information (CCI).
Authenticate Users for Secure Video Sharing
User authentication through an identity and access management (IAM) system helps in private video sharing. By uploading private videos on a secure video sharing platform, you can create a wall between your enterprise video content and the people attempting to access it.
This approach works like a gatekeeper asking for an ID from the person trying to get inside. When a user attempts to access the video, the system verifies whether the person is who they are claiming to be.
Authenticating users for securely sharing videos online is a practical approach, especially since 41% of cyberattacks involve stealing user credentials. This technique is applicable in the following cases:
- The sensitivity of video content is moderate or high.
- You want to share multiple videos with different people over time.
- The type of information is internal or confidential.
- The video content may or may not fall under the scope of compliance.
- There may be a low or a high risk of unauthorized access, depending on the video.
- The implications of unwarranted access are moderate to high.
For instance, company video updates, internal communications videos, video recordings of patient-physician communications, etc., should be accessed through user authentication.
Define a Custom Security Policy
In cases when predefined permissions and access levels are not enough for secure video sharing, you need to be able to define your own security policy that applies to every single video stored in your enterprise video platform.
Defining a custom security policy for private video sharing is ideal in the following cases:
- The sensitivity of video content varies from low to high.
- You want to share multiple videos with multiple people over time.
- The type of information is internal or confidential.
- Some videos fall under the scope of compliance, while others do not.
- There is a low to high risk of unauthorized access, depending on the content.
- The implications of unwarranted access are reputational risk and information breach.
- The company’s data sharing policy has specific secure video sharing requirements.
This practice applies to all video content stored within your organization’s systems, in case your company has a unique data-sharing policy in place. The video content can range from less sensitive recordings of daily standup meetings to highly sensitive CEO communications videos, internal company updates, and patient consultation and experience videos.
Enable IP and Location Restrictions
Applying restrictions based on IP addresses and locations is another effective means for private video sharing. This helps you avoid unwanted users from a particular region accessing your private video content.
We recommend going for IP and location restrictions to share private videos in the following cases:
- The sensitivity of video content is high.
- The video recipients are mostly internal from within your organization.
- The type of information is internal, confidential, or used for commercial purposes.
- Videos either fall under regional compliances or are protected by copyright laws.
- There is a high risk of unauthorized access from countries infamous for cyberattacks.
- The implications of unwarranted access to private video content are severe.
For instance, a class instructor showing a copyrighted movie for learning purposes in a virtual training video in the US will have to restrict it to the region to avoid copyright hassles. Although it is considered fair use according to the US copyright law, the US copyright law does not apply outside the region.
Blacklist Domains for Secure Media Embedding
Automated content-stealing sites are becoming quite common, and content scraping has become the norm. These websites shamelessly steal content and market it as their own. Imagine spending hours perfecting the video you want to show to your external audience, and someone copies it. Frustrating, right?
Blacklisting certain domains for secure video sharing is quite helpful in the following cases:
- The sensitivity of video content can be low or high.
- The video content is intended for sharing with individuals outside your organization.
- The type of information is public, but it needs to be protected from content theft.
- The video content may not fall under the scope of compliance.
- There is a fair risk of unauthorized access in the form of content theft by other sites.
- The implications of unwarranted access are lost revenue and opportunities.
- Not restricting the video download can lead to unauthorized spread of the content.
For instance, a teaser video of a virtual event or webinar, or the event recording itself, can be stolen by content-stealing sites, thereby hurting the business in terms of not attracting the right audience through the intended channel.
Share Videos with Encrypted Video Sharing
Encrypted video sharing is the process to secure enterprise video content over an encrypted network when the data is in motion or at rest. Content encryption is one of the most popular techniques for secure video sharing. This encryption for video content delivery prevents interception or data breaches and results in a complete video content security for sensitive communications.
With advanced encryption technologies widely available now, such as AES and TLS encryption, you can share enterprise video content without the fear of spoofing attacks.
- Encrypted video sharing is a reliable means for privately sharing videos in the following cases:
- The sensitivity of video content is moderate, high, or extremely high.
- The video content is preferably shared with an external audience.
- The type of information is confidential and restricted.
- The video content may be subject to data privacy compliance.
- There is a fair chance of unauthorized access.
- The implications of unwarranted access are leakage of communications and secrets.
For instance, you might encrypt and securely share internal communications videos involving senior management with critical shareholders and investors to gain their confidence in the company.
Redact Sensitive Content from Videos
Redaction is used to hide sensitive information from video/audio recordings for secure video sharing.
This technique helps protect personally identifiable information (PII), protected health information (PHI), business identifiable information (BII), and trade secrets found in video recordings.
With advanced AI-powered enterprise video platforms available, the redaction workflows are automated.
The redaction technique is quite effective for private video sharing in the following cases:
- The sensitivity of video content is extremely high.
- The video content is to be shared with both internal and external users.
- The type of information is restricted as per the business data classification level.
- The video content is subject to data compliance like GDPR, CCPA, and HIPAA.
- There is a high chance of unauthorized access by hackers.
- The implications of undue access are a threat to physical and psychological safety.
For instance, videos involving health-related data of patients, such as HIPAA identifiers, need to be redacted before securely sharing them internally for patient education and research purposes and externally with law enforcement agencies.
Restrict Downloading of Videos
Preventing the shared video content from being downloaded is the last but not least important means of secure video sharing. This prevents the unwanted distribution of enterprise video content by the intended recipient of the shared video.
Restricting the downloading of videos seems a viable solution in the following cases:
- The sensitivity of video content is moderate to high.
- The video content is to be shared with external users who cannot be trusted.
- The type of information is internal and confidential.
- The video content may not be subject to compliance.
- You want others to only view the video and do nothing else with it.
- There is a fair chance of the unauthorized distribution of video content.
- The implications of unwarranted access to video content are moderate.
- Making the video available for download can lead to unwanted spread.
For instance, you need to prevent videos involving proprietary business information from being downloaded to control the spread of the data.
Which Secure Video Sharing Method Is Best for Enterprises?
There is no single answer. Deciding which method to go for depends on several factors that have been discussed above, such as the nature of the content being shared, the intended audience, the compliances that the video is subject to, the implications of unauthorized access, the risks involved, and other factors as well.
This is why we have picked the ten best practices for you to follow for secure video sharing, so that you do not have to think about which method works best for you.
Secure your Video Sharing with EnterpriseTube
Secure video technologies are no longer optional—they’re a necessity. EnterpriseTube helps address this by providing a structured, policy-driven environment for secure video content delivery. The platform supports every stage of private video sharing—from upload and storage to controlled distribution—ensuring that only the right people can access the right videos.
With encrypted video sharing, identity-based access, and detailed permission settings, EnterpriseTube allows teams to safeguard their secure video files without adding complexity to daily workflows. Features such as temporary access links, download restrictions, and audit logs help organizations meet internal and regulatory standards while maintaining ease of collaboration.
Designed for flexibility, EnterpriseTube adapts to different use cases, whether it’s sharing internal training sessions, client presentations, or compliance-related recordings. Its combination of secure online video sharing, role-based access control, and centralized governance helps organizations build lasting confidence in how they manage and share video content across departments.
Key Takeaways
- Secure video sharing depends on sensitivity, compliance, and access level.
- Enterprises should combine authentication, encryption, and restricted access.
- Temporary links, download restrictions, and redaction add layered protection.
- EnterpriseTube enables policy-driven, secure video content delivery.
People Also Ask
Secure video sharing (also called secured video distribution) is the protected distribution of video content. This is made possible by using measures like passwords and encryption to prevent unauthorized access and data leaks, crucial for safeguarding business and patient information.
To securely share a video externally, use a combination of methods such as temporary access links that expire after a set time, password protection, and encryption. For high sensitivity, add IP restrictions and disable downloads to control distribution.
A secure video sharing platform for enterprises should have key features that include end-to-end encryption, granular access controls, user authentication, password protection, and compliance with standards like HIPAA and GDPR.
Password protection acts as a gatekeeper, requiring a code to access the video file or stream, while encryption scrambles the video data itself, making it unreadable even if intercepted. Password protection controls who can enter, while encryption ensures the content is secure even if intercepted.
Access control is crucial because it enforces the principle of least privilege, ensuring users can only view the content necessary for their role while minimizing insider threats and limiting damage from compromised accounts.
Temporary video sharing enhances security by limiting access to a video for a specific duration or a set number of views. Ideal for time-sensitive materials like investor updates or confidential project briefings.
Redaction permanently obscures sensitive information within a video, such as faces, license plates, or on-screen text containing personal data, which is essential for complying with privacy laws like HIPAA and GDPR.
A secure video platform aids compliance by providing specific features like audit logs to track access, robust encryption, user authentication, and data redaction tools. It provides required features like audit logs, encryption, and redaction tools to meet data protection standards in regulations.
Jump to
You May Also Like
These Related Stories
Video Content Delivery System: How CDNs Power Secure Live Video Streaming

The Best Way to Share Videos Online Privately and Securely



No Comments Yet
Let us know what you think